A growing phishing method known as “Browser-in-the-Browser” is being used by hackers in new attacks to obtain Steam user credentials. A popular attack technique called “Browser-in-the-Browser” involves the construction of false browser windows inside the open window, which are then made to look like sign-in pop-up pages for certain login services.
The first publication to cover the capabilities of this new phishing kit developed by security researcher Mr.d0x was BleepingComputer in March 2022. Threat actors can develop bogus login pages for Google, Microsoft, Steam, and other services by using this phishing kit.

In a recent study on the subject, Group-IB shows how a new campaign using the “Browser-in-the-Browser” technique targets Steam users, namely professional gamer accounts.
Some well-known Steam accounts are valued between $100,000 and $300,000, and these phishing attacks seek to sell access to those accounts.
The phishing kit utilized in the Steam campaign was not readily accessible in hacking forums or dark web marketplaces, according to Group-IB. Instead, hackers who collaborate in private on Telegram or Discord channels to plan their attacks use it.
Direct messages on Steam are sent to potential victims encouraging them to join a team for LoL, CS, Dota 2, or PUBG tournaments. The targets will get at a phishing site for what looks to be an entity sponsoring and staging esports competitions via the links sent by the phishing actors.
Visitors are required to sign in using their Steam accounts to join a team and participate in a competition. The new login page window, however, is a false window made inside the current page, making it exceedingly difficult to identify as a phishing assault. It is not a genuine browser window layered over the original website.
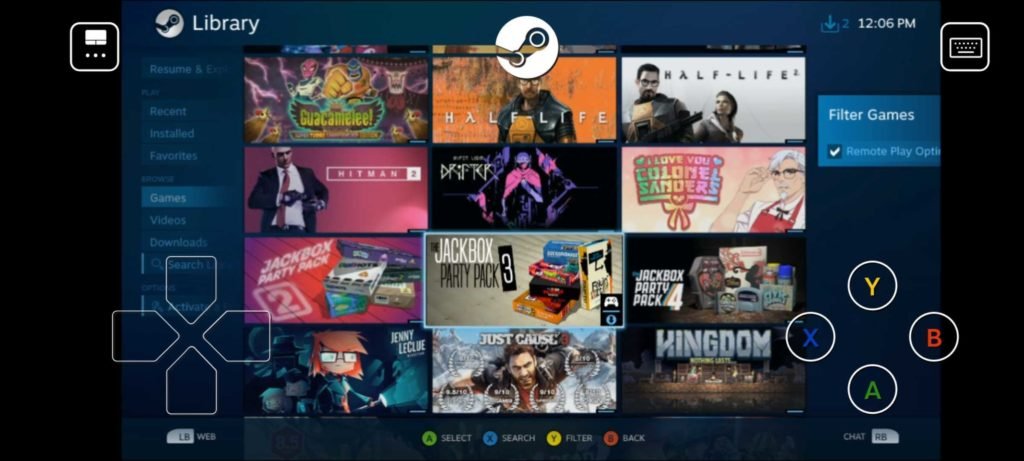
The landing pages even support 27 different languages, automatically determining the victim’s preferred language based on browser settings and loading it. The victim is then prompted to submit the 2FA code on a new form after entering their credentials. A notice appears if the second step is failed.
To reduce the possibility that the victim would become aware of the intrusion, the user is normally routed to a URL supplied by the C2 if the authentication is successful.
The victim’s login information has already been taken and delivered to the threat actors at this stage. Similar assaults involve fast account takeovers by threat actors who then modify the victims’ email addresses and passwords to make it more challenging for them to regain control of their accounts.
Because the method needs JavaScript, deliberately blocking JS scripts would stop the bogus login from appearing. Most individuals do not, however, block JavaScript because doing so would ruin numerous popular websites.
In general, be extremely cautious when clicking links offered by strangers in direct messages you get on platforms like Steam, Discord, or others that are dedicated to video games.
Also read:
Ubisoft to release Season 10 of The Division on September 13th, 2022


